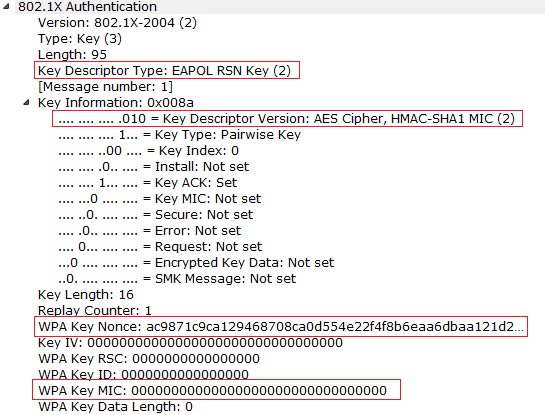
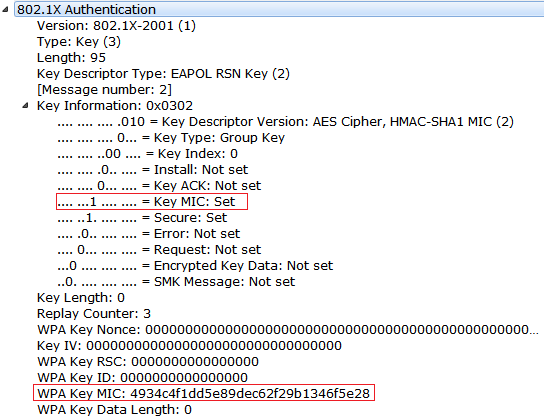
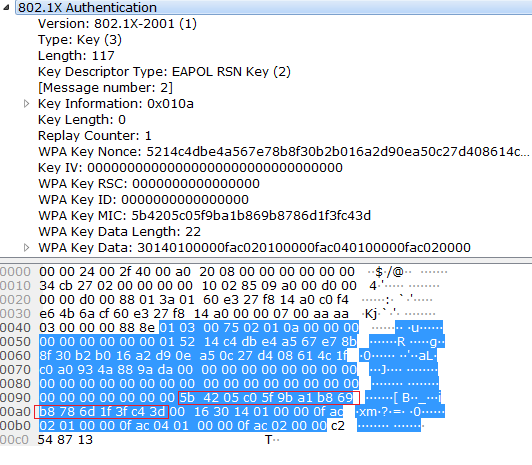
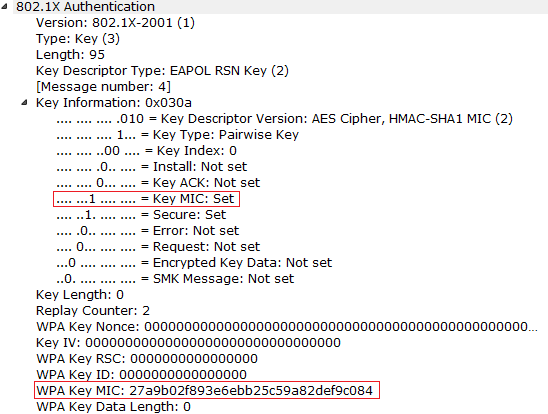
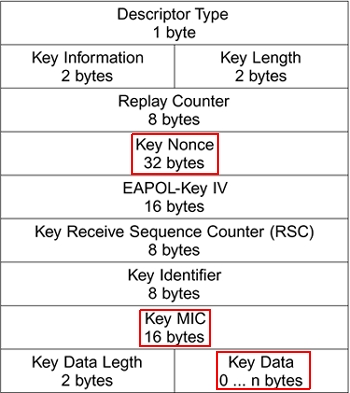
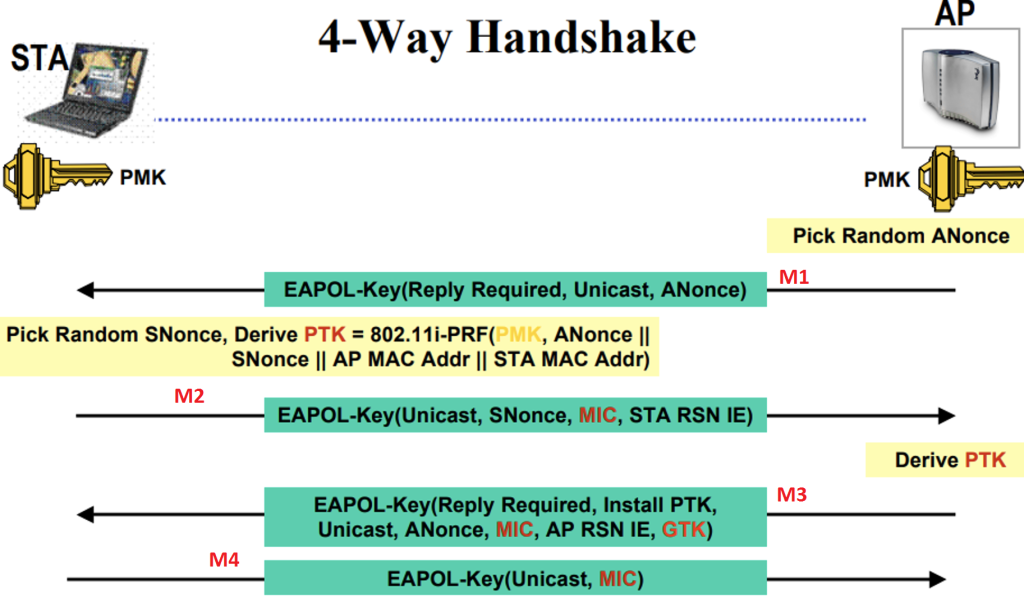
pbkdf2 - WPA/WPA2 Handshake -- A question on the computation of the MIC - Information Security Stack Exchange
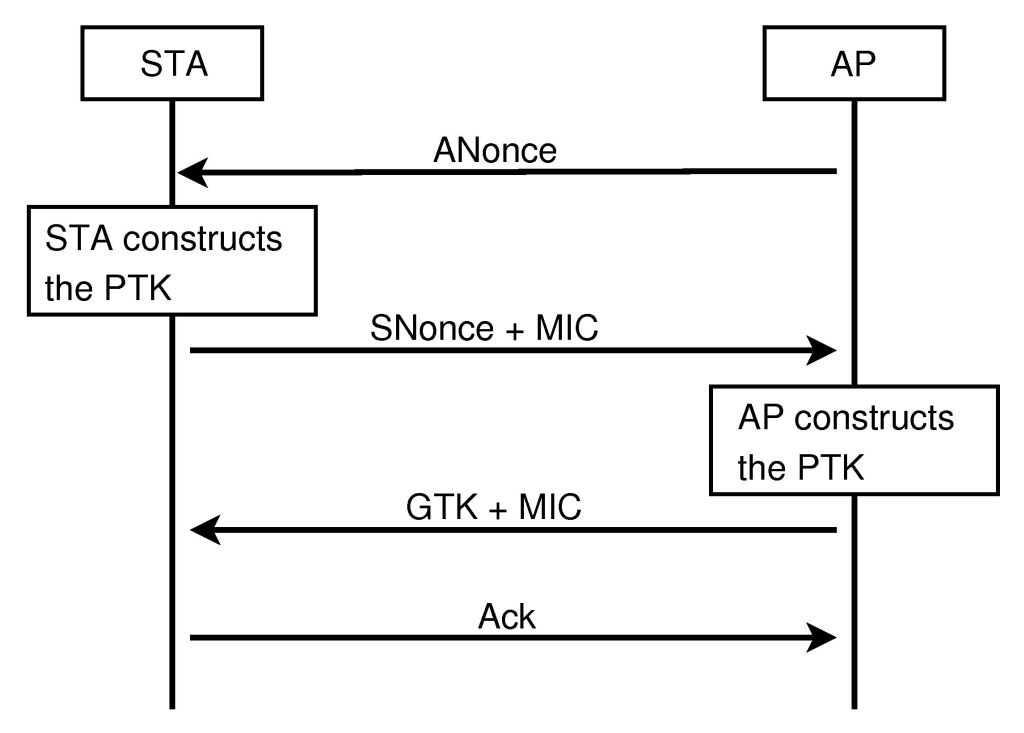
First Message of the WPA Four-way Handshake (ANonce and AP MAC Address)... | Download Scientific Diagram

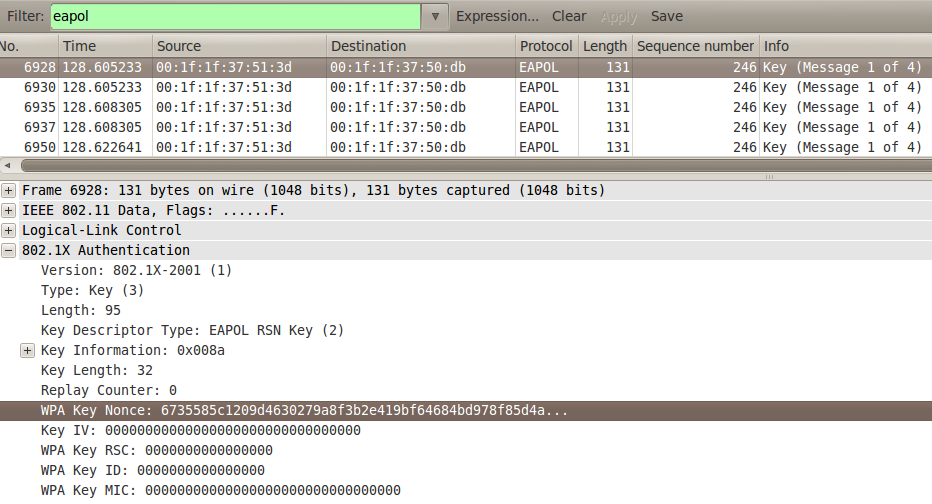
pbkdf2 - WPA/WPA2 Handshake -- A question on the computation of the MIC - Information Security Stack Exchange

Figure 4 from Secure key exchange scheme for WPA/WPA2-PSK using public key cryptography | Semantic Scholar