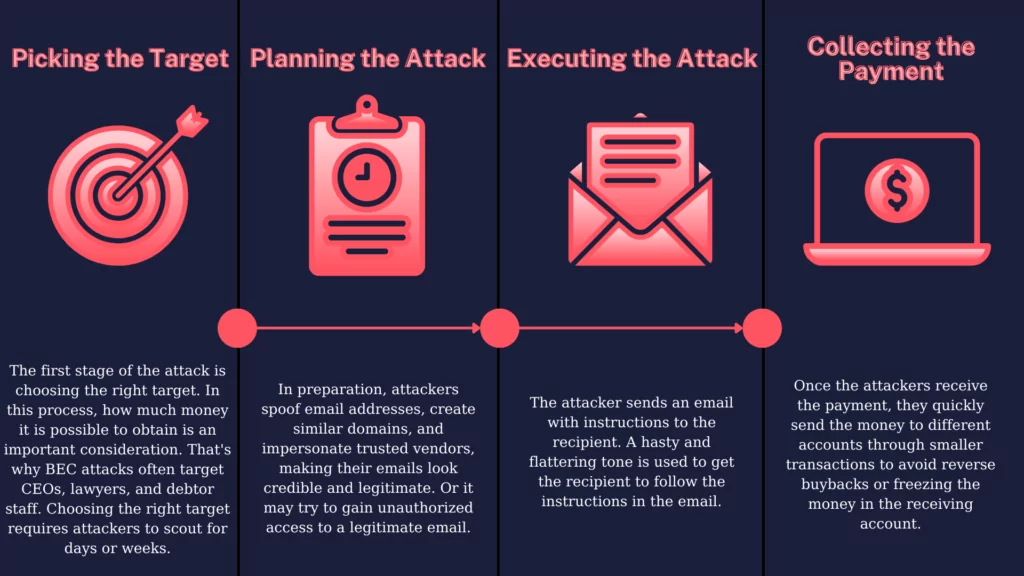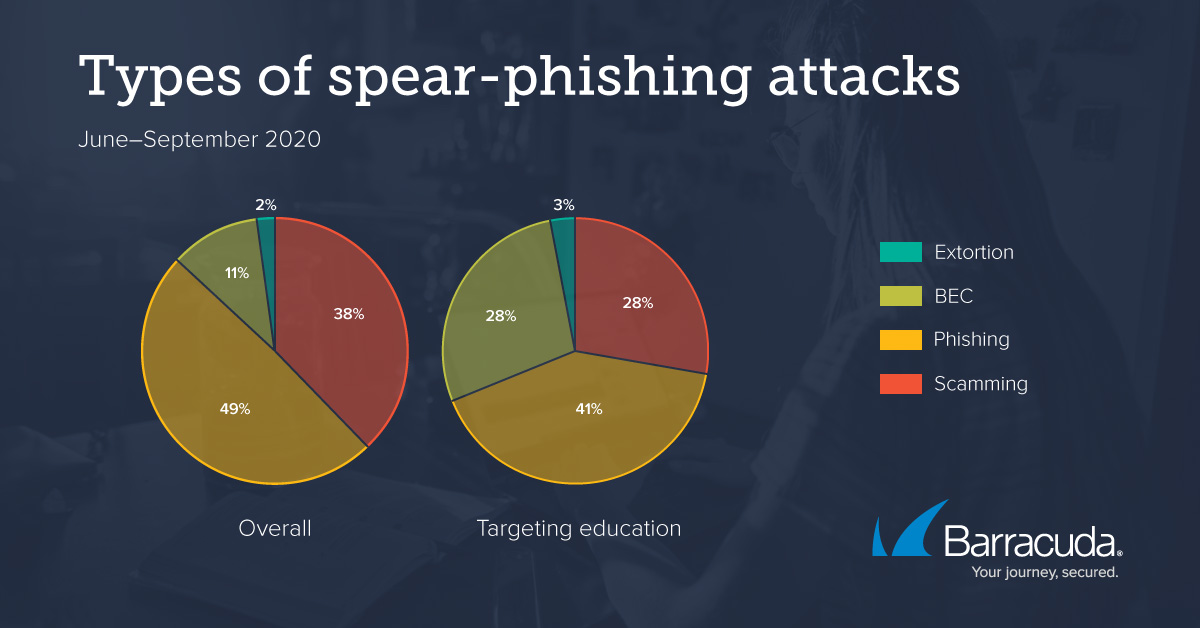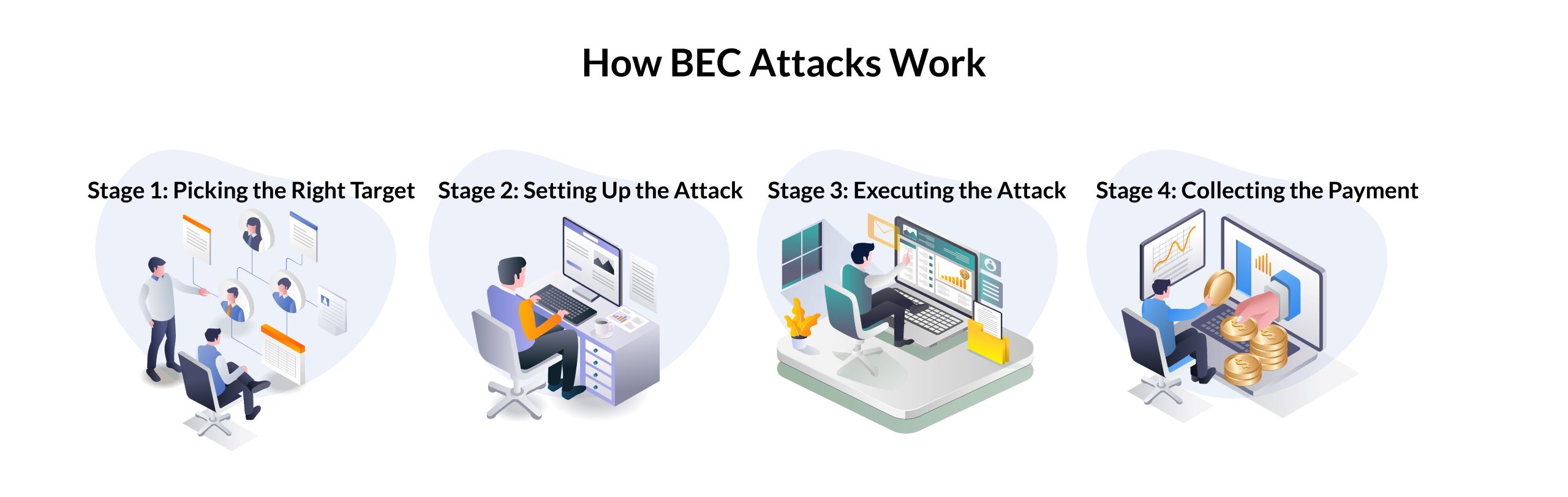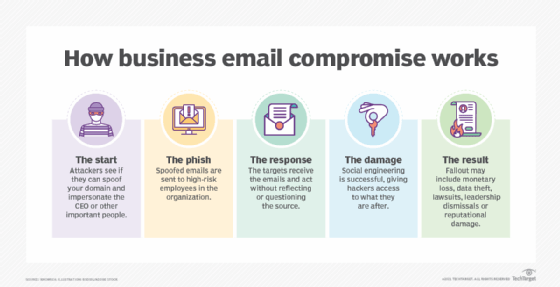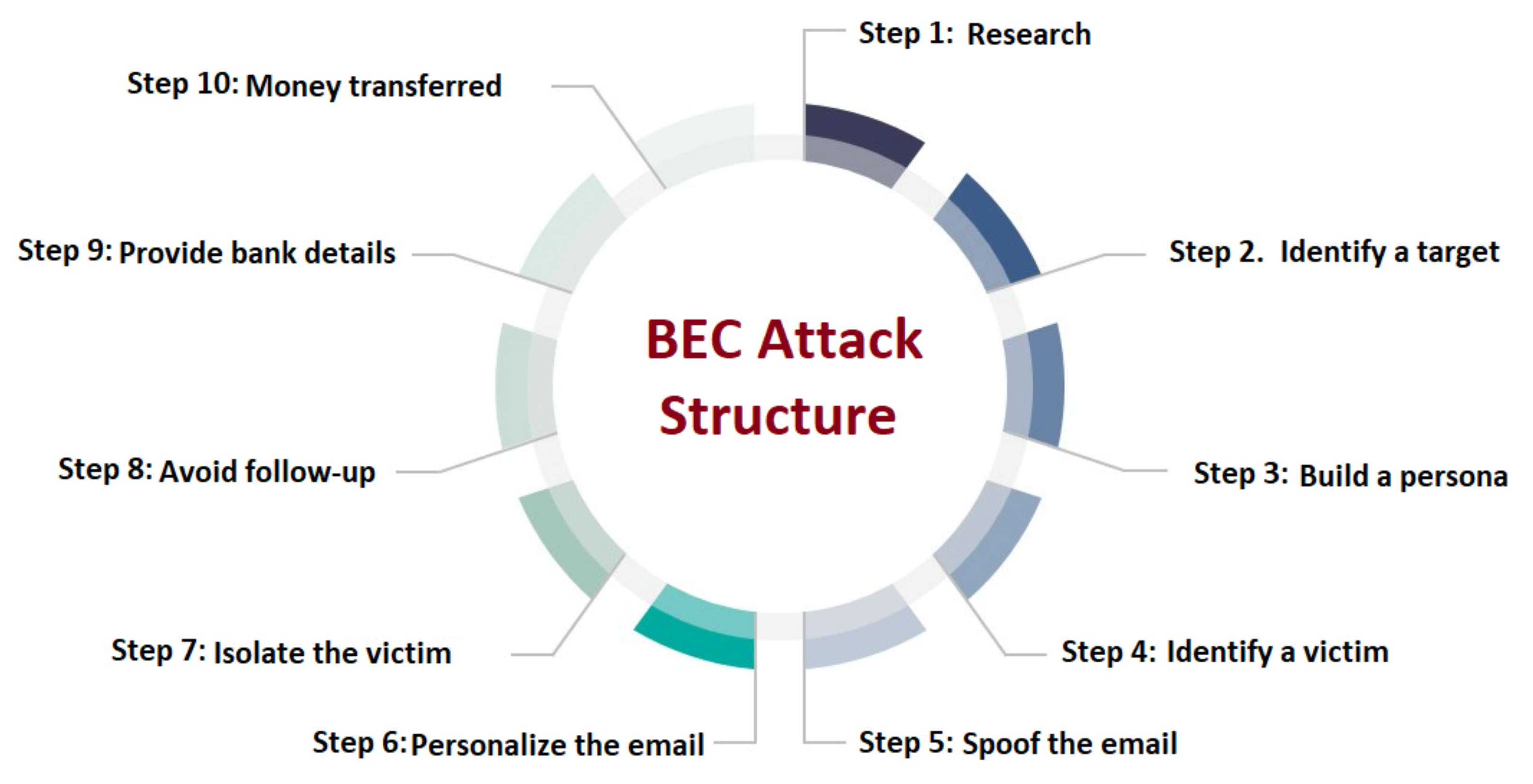
Electronics | Free Full-Text | Business Email Compromise Phishing Detection Based on Machine Learning: A Systematic Literature Review

Behind the scenes of business email compromise: Using cross-domain threat data to disrupt a large BEC campaign | Microsoft Security Blog